Solutions for Hardware tasks.
YauzaCTF 2021 Hardware
Not so long ago, the YauzaCTF2021 contest ended, in which I took part as a member of the “Unicorn Team” team, here I outlined my solutions for problems of the Hardware category.
YauzaCryptoModule
Description:
Russian: На этот раз мы изучим не просто устройство, а полноценный крипто-модуль! Вам потребуется провести его анализ и найти флаг
English: This time we will study not just a device, but a full-fledged crypto-module! You will need to analyze it and find the flag
Attach: Crypto.sal
This is the first task that I started solving after the start of competition. I tried to open the attached file using an archiver (binwalk showed 7z signatures), pulled out a description in json format. After studying it, I realized that this is a standard project file of some software for collecting information from some sensors. Googling it, I immediately found logic 2 tool for saleae devices. Later I found out that this information was contained in the description of task 1337-6.
Having opened the provided file in logic 2, I analyzed its contents for some time and looked for the protocols known to me. At first, my attention switched to channels 0 and 1, which turned out to be uart channels rx tx.
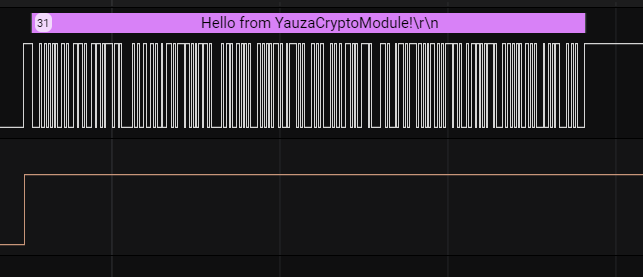
Applying the uart analyzer with standard parameters to these channels, I got the text:
TX: Hello from YauzaCryptoModule!
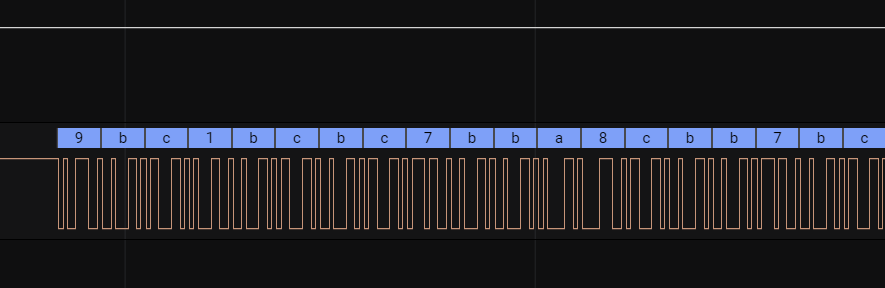
RX: 9bc1bcbc7bba8cbb7bcbba7bc08cbbc0ba7dd6cf8cbfd47dcbd48c7dbb8cd67cc08c808cced880cf_
TX: Got it!
TX: 9bc1bcbc7bba8cbb7bcbba7bc08cbbc0ba7dd6cf8cbfd47dcbd48c7dbb8cd67cc08c808cced880cf
TX: Starting to encode it...
RX: a5cdc1c2cdaba0aec3d480bad0bf80ba7ba7bcc1c2c27d7bc9_
From the text it becomes clear that the input data is sent to the “Cryptomodule” in Hex format with the end of the message symbol _. Let’s continue the analysis.
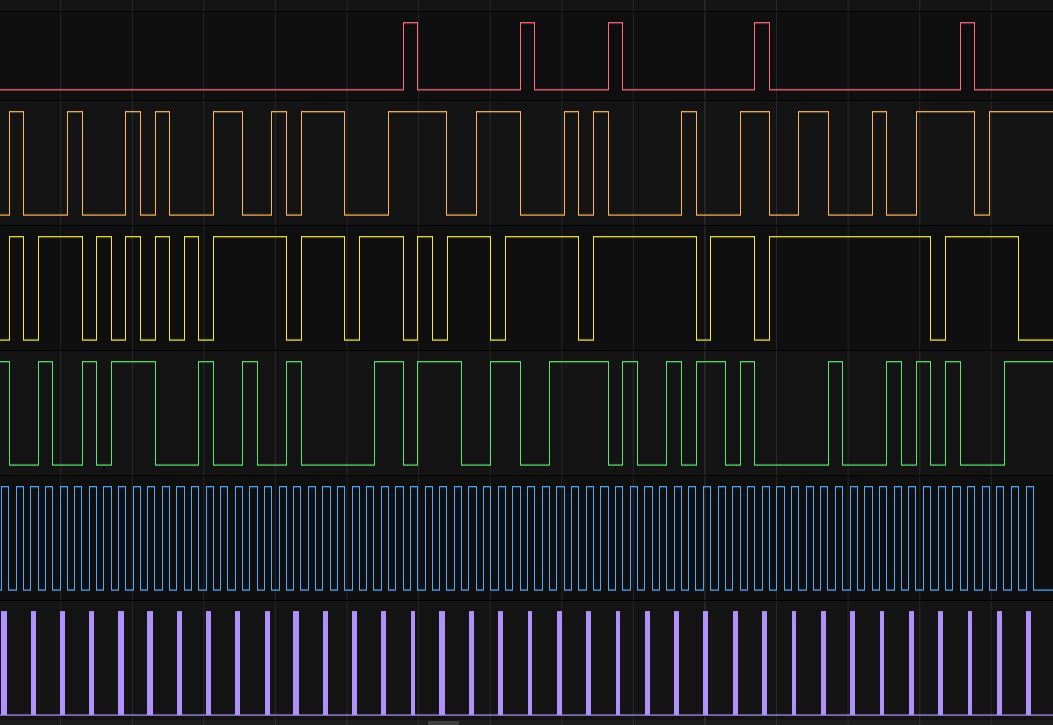
We have 5 seemingly synchronized channels, the first 3 do not seem to contain useful information, let’s take a closer look at channels 6 and 7.
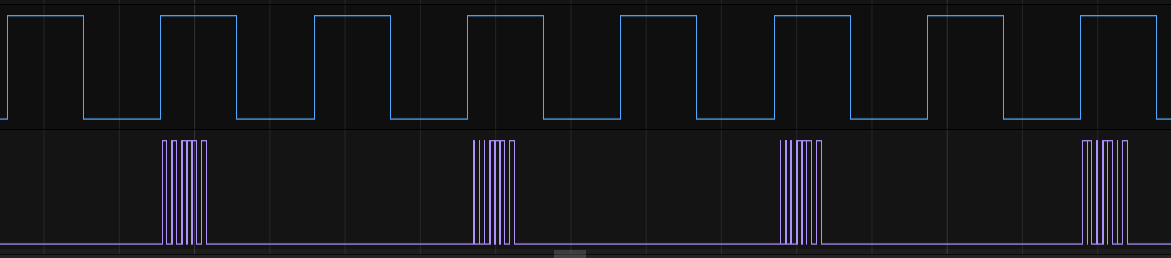
We have a protocol in which every second peak of channel 6 means the start of data transmission on channel 7, 8 information bits and 1 stop signal are transmitted in channel 7.
I wanted to write an analyzer in order to parse this data automatically, but unfortunately logic 2 has some problems with low-level analyzers written in Python, they are not displayed in the selection panel. Even the analyzers from the repository with examples do not work :/
So I rewrote the transmitted bits manually:
1100101 1010111 0000111 0000111 1100110 0100111 0000010 1100111 1100110 1100011 0100111 1100110 0010111 0000010 1100111 0010111 0100111 1000110 0111011 1110011 0000010 1110111 0001011 1000110 1100011 0001011 0000010 1000110 1100111 0000010 0111011 0000110 0010111 0000010 0010110 0000010 0110011 0011011 0010110 1110011
Pulled the transmitted data:
>>> data = "1100101 1010111 0000111 0000111 1100110 0100111 0000010 1100111 1100110 1100011 0100111 1100110 0010111 0000010 1100111 0010111 0100111 1000110 0111011 1110011 0000010 1110111 0001011 1000110 1100011 0001011 0000010 1000110 1100111 0000010 0111011 0000110 0010111 0000010 0010110 0000010 0110011 0011011 0010110 1110011"
>>> data = "".join(list(map(lambda x: chr(int(x[::-1],2)),data.split(" "))))
>>> data
'Supp3r s3cr3t str1ng wh1ch 1s n0t 4 fl4g'
Let’s go back to the protocol, as we remember, a string in hex was transmitted to the cryptomodule via uart, if we try to match this string and data from channel 7, we will find a one-to-one correspondence of character substitution! Apparently our task is to decipher the second transmitted string.
After this stage, I tried to select the parameters of the function responsible for the replacement, but to no avail. So I tried to make an alphabet of replacing characters on the existing string and this is what happened:
>>> data = 'Supp3r s3cr3t str1ng wh1ch 1s n0t 4 fl4g'
>>>
>>> alph = {}
>>> enc = b"".fromhex("9bc1bcbc7bba8cbb7bcbba7bc08cbbc0ba7dd6cf8cbfd47dcbd48c7dbb8cd67cc08c808cced880cf")
>>> for i in range(len(enc)):
... alph[enc[i]] = data[i]
...
>>> alph
{155: 'S', 193: 'u', 188: 'p', 123: '3', 186: 'r', 140: ' ', 187: 's', 203: 'c', 192: 't', 125: '1', 214: 'n', 207: 'g', 191: 'w', 212: 'h', 124: '0', 128: '4', 206: 'f', 216: 'l'}
attempt to decrypt the next strings…
>>> flag = b"".fromhex("a5cdc1c2cdaba0aec3d480bad0bf80ba7ba7bcc1c2c27d7bc9")
>>> for i in range(len(flag)):
... if(flag[i] in alph.keys()):
... print(alph[flag[i]],end="")
... else:
... print("?",end="")
...
??u??????h4r?w4r3?pu??13?>>>
Let’s extend the alphabet because of the well-known flag format:
>>> alph[flag[0]] = 'Y'
>>> alph[flag[1]] = 'a'
>>> alph[flag[3]] = 'z'
>>> alph[flag[5]] = 'C'
>>> alph[flag[6]] = 'T'
>>> alph[flag[7]] = 'F'
>>> alph[flag[8]] = '{'
>>> alph[flag[-1]] = '}'
>>> for i in range(len(flag)):
... if(flag[i] in alph.keys()):
... print(alph[flag[i]],end="")
... else:
... print("?",end="")
...
YauzaCTF{h4r?w4r3?puzz13}
And flag is YauzaCTF{h4rdw4r3_puzz13}
KeyLeak
Description:
Russian: Нам в руки попала подозрительная клавиатура, у которой на некоторых пинах обнаружена интересная активность. Чем же она нас так заинтересовала?
English: We got our hands on a suspicious keyboard with interesting activity on some pins. Why is she so interested in us?
Attach: Keyboard.sal
Open the attached file in an already known program. Immediately after opening, we see channel 4 very similar to uart. The analyzer could not analyze the data in the standard configuration, but by changing the buadrate value to 115200, we see a readable text.
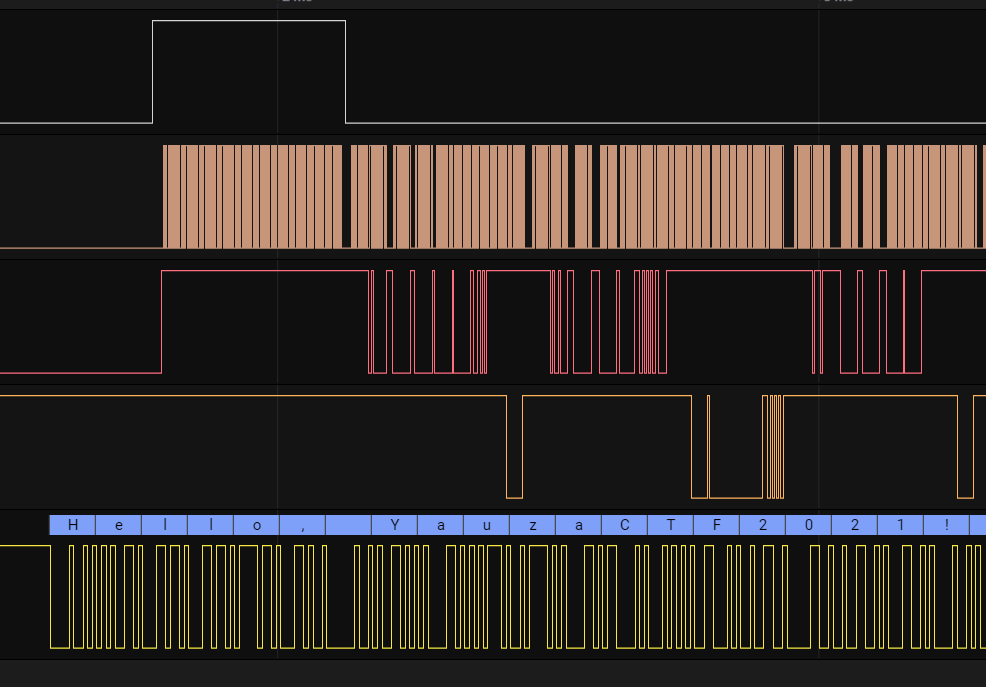
Hello, YauzaCTF2021!!!
Wiring is correct and a card is present.
Card type: SDHC
Clusters: 947328
Blocks x Cluster: 64
Total Blocks: 60628992
Volume type is: FAT32
Volume size (Kb): 30314496
Volume size (Mb): 29604
Volume size (Gb): 28.91
Initializing SD card...initialization done.
flag.txt: https://bit.ly/3y3bYwR
By clicking on the link, we find that this is a Rickroll :)
Let’s continue the analysis, the message text contains information about the initialization of the SDHC card. This is a good hint about the protocol used - SPI.
Trying to use the analyzer. Clock-Channel 1, MOSI channel 2, MISO channel 3, CS or Enable-Channel 0.
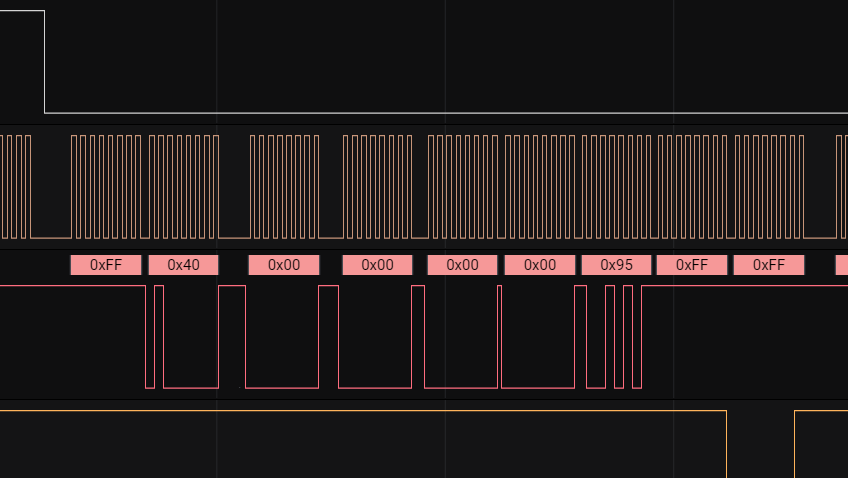
As follows from the hint, the protocol on top of SPI - SDMMC. We use the extension from the repository to parse SDMMC commands.
We pull out the data that follows after the read command.
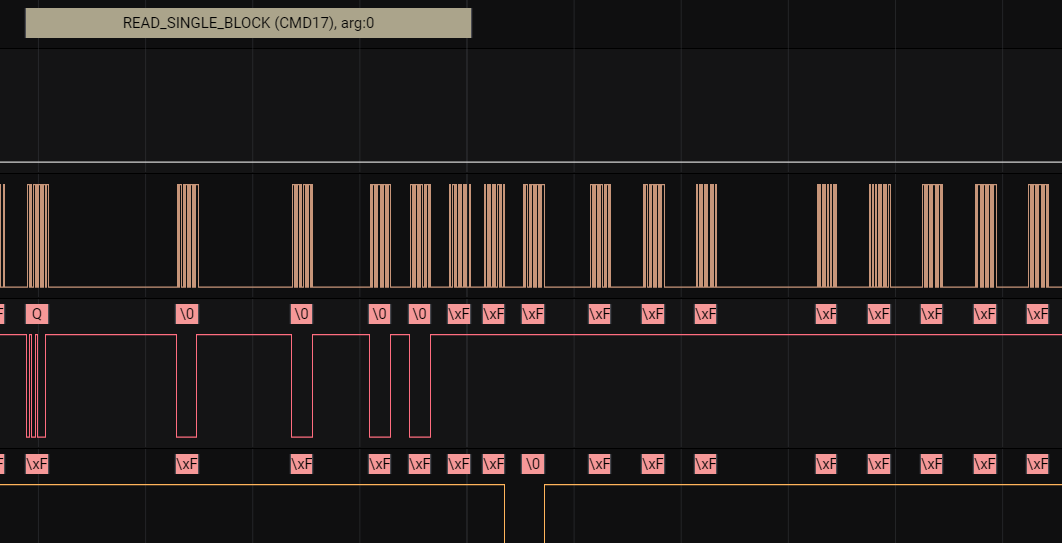
And found flag: YauzaCTF{$D_SP1d3r}
1337-6
Description:
Russian: странное описание задания с намеком на хакерское число 1331 и софт SALEAE (не забыть поменять). Формат флага: YauzaCTF{}
English: strange job description with a hint of the hacker number 1331 and saleae software (remember to change). Flag format: YauzaCTF{}
Hint: SSD(1337-6)
Attach: 1331.sal
When I started solving this problem, I could not understand for a long time what protocol is used for interaction. After 2 hours of studying, I decided to carefully read the description and paid attention to the number 1331, some time after that I found the SSD1331 lcd display, which was later mentioned in the hint. However, even after I found out with which device the interaction is carried out, it was a mystery to me which protocol is used.
The reason is that for a long time I could not find the time channel that should be present in the standard SPI mode used for interacting with displays. My mistake was to believe that the signals from the clock should be symmetrical and the same.
Adding a hint, I finally made sure that I was thinking correctly, and decided to try some channel as a clock. The main candidate was Channel 3. it worked!
In the next it was a matter of technique, I found a driver library for this display, made sure that the commands match and extracted the data to parse them and draw a picture.
